Security & Compliance
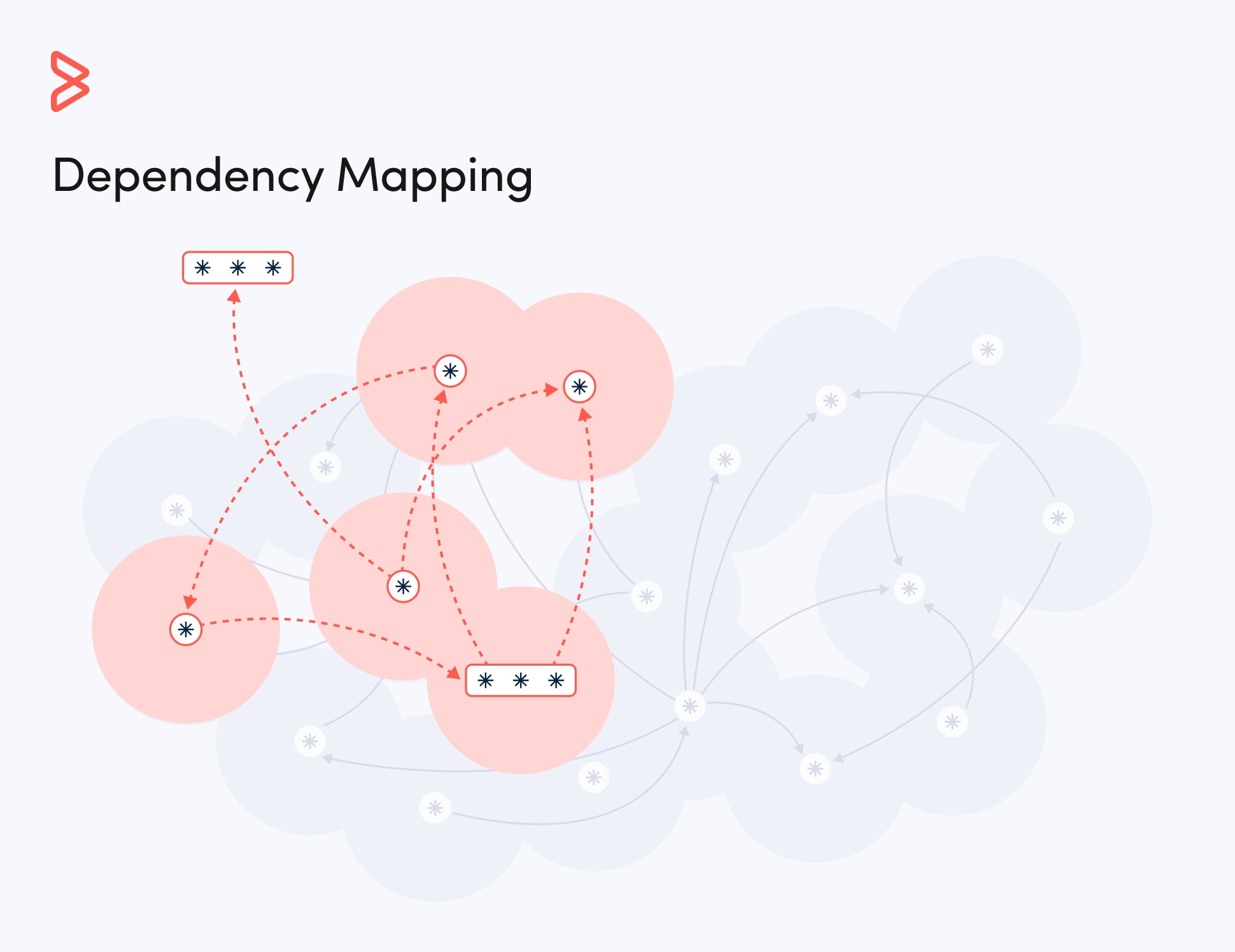
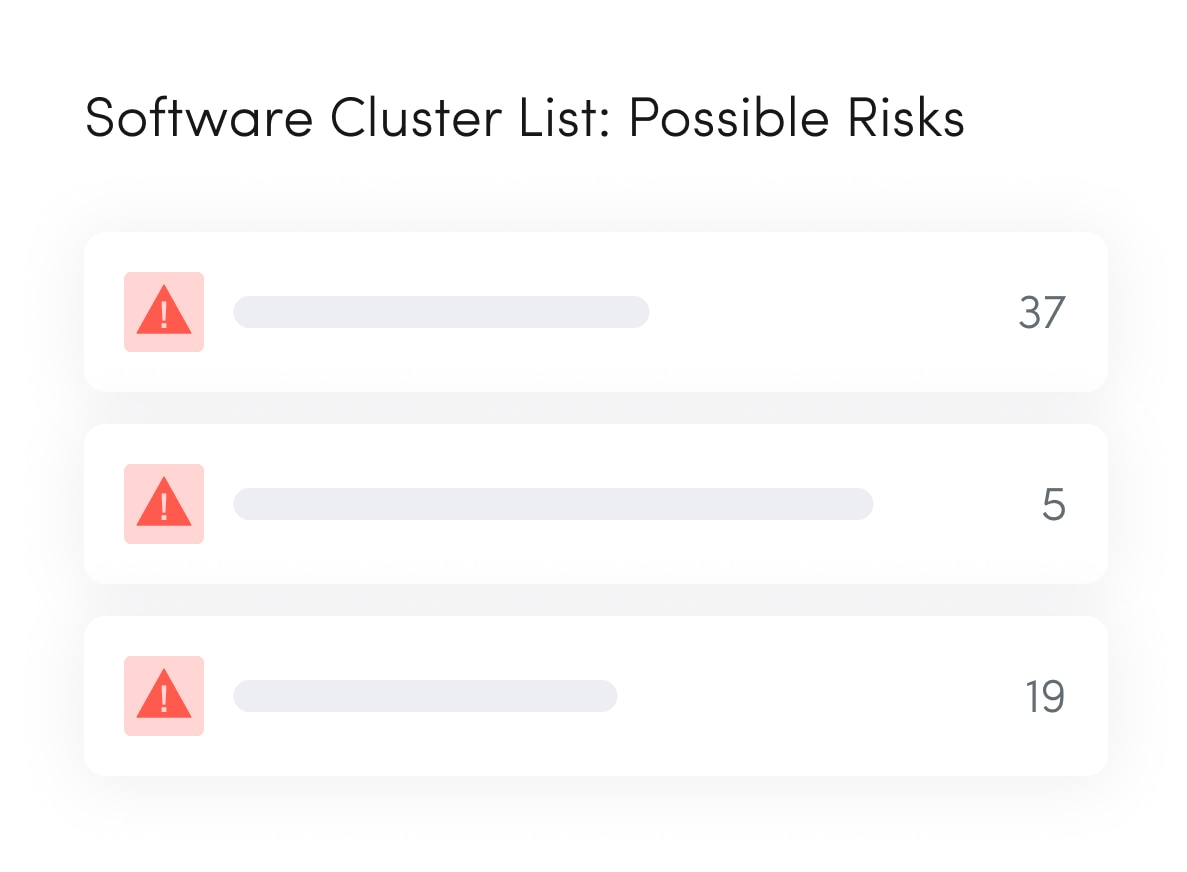
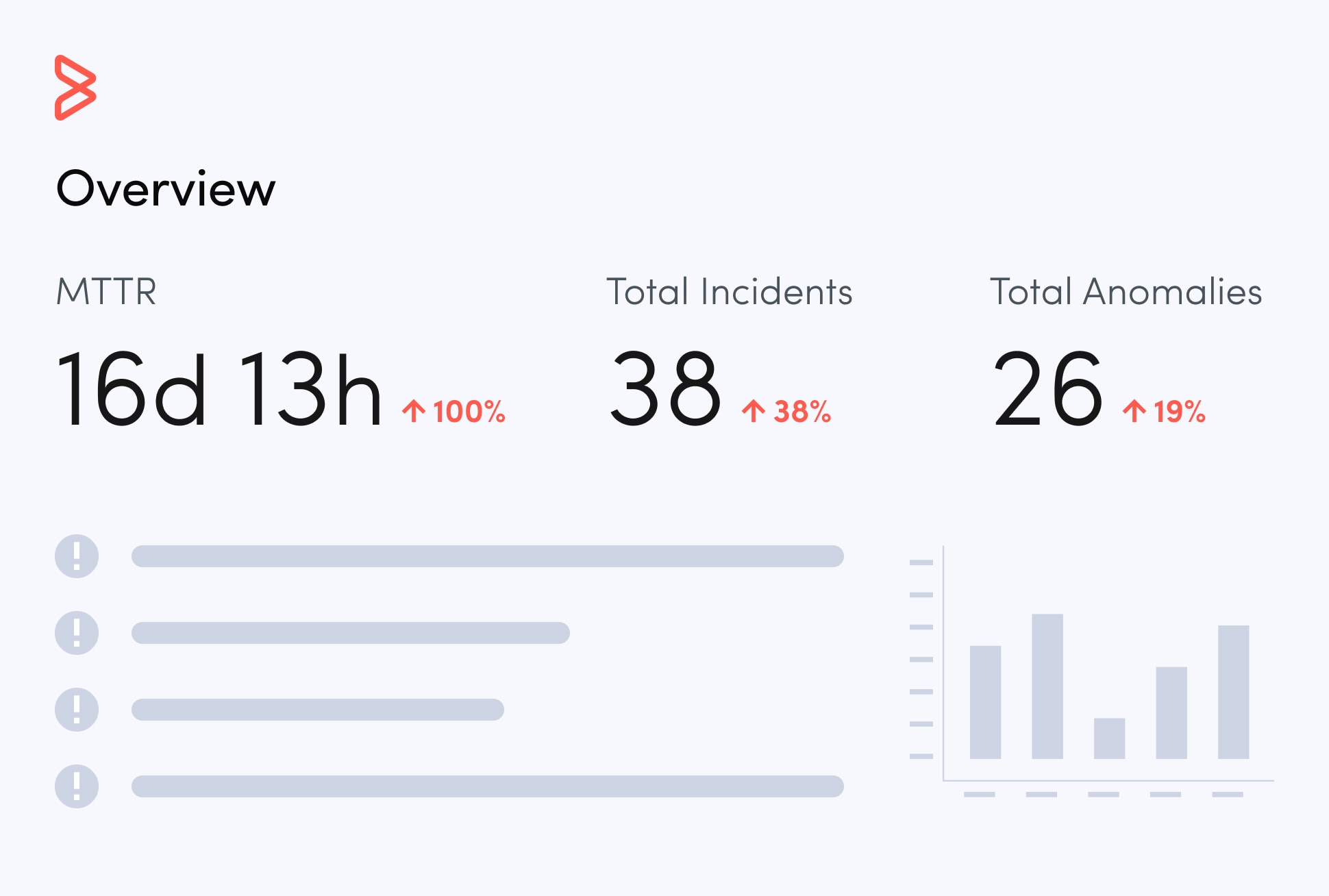
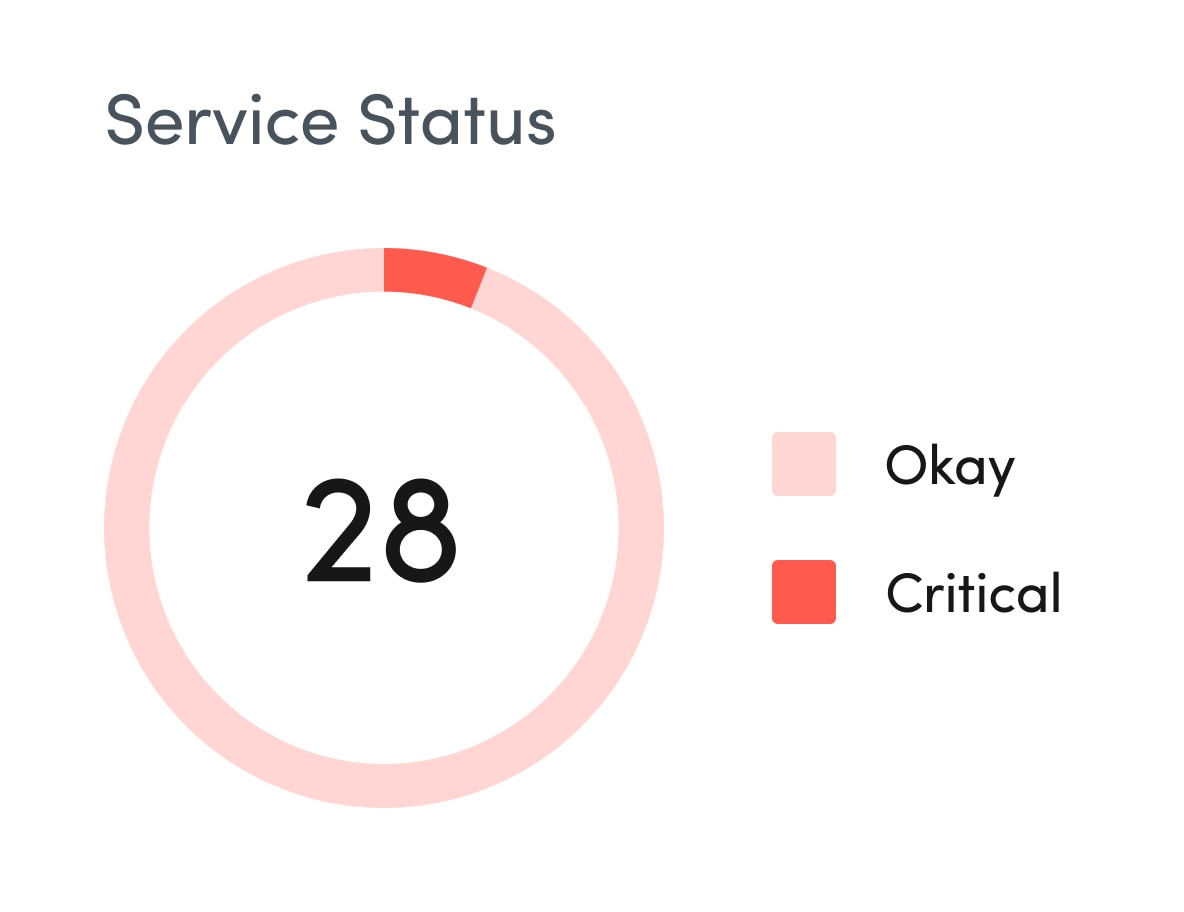
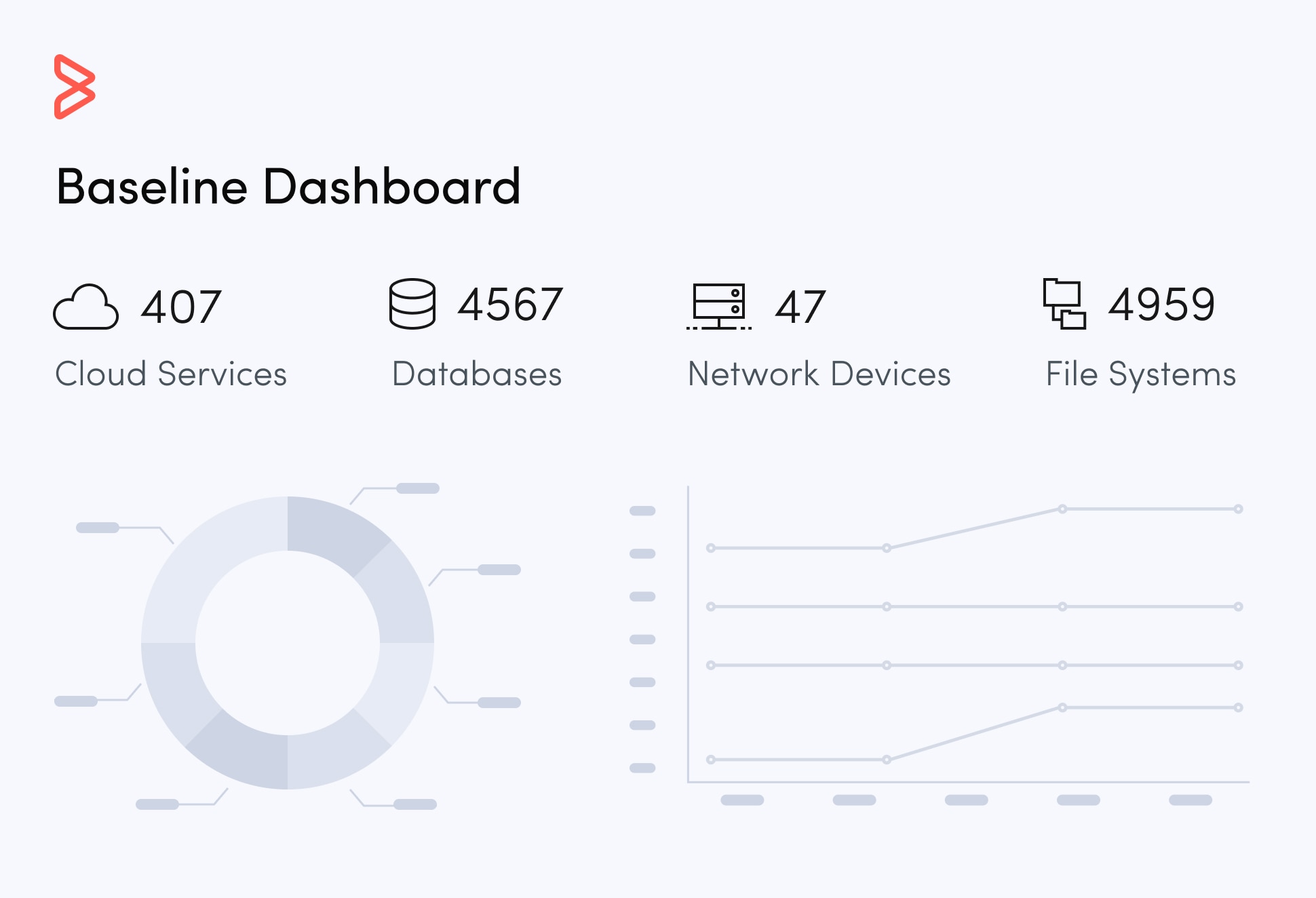
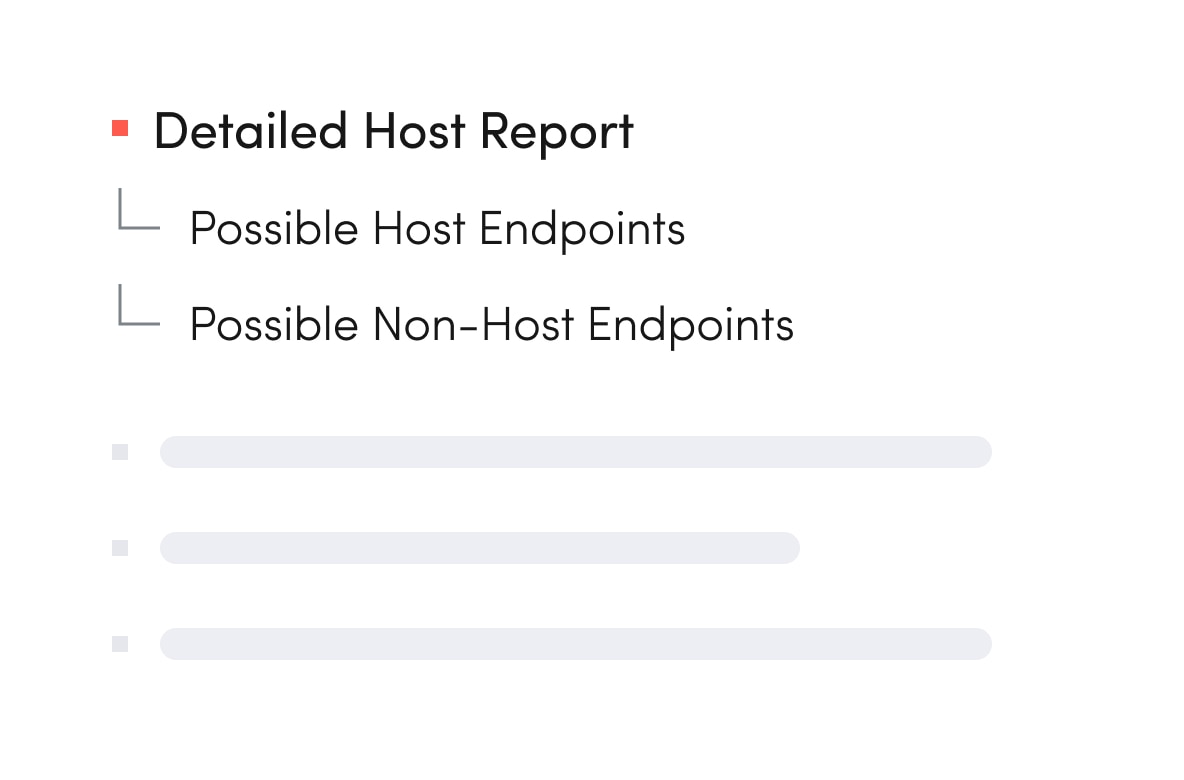
IT security teams face relentless pressure from both internal and external sources as the number and intensity of security attacks continue to grow. Thanks to shadow IT, sensitive data now lives everywhere. Unidentified, unused applications and inactive devices open penetration points for security attacks, while third-party software, open-source inventory, and assets that lie unsecured outside the datacenter introduce additional risk.
Learn more